Security Fatigue is Real and It’s Weakening Your Defenses
Overloaded employees are tuning out security warnings. Learn why security fatigue matters and how to build resilience into your defenses.
The Warning That Gets Ignored
A finance employee receives her third phishing warning of the week. The pop-up says, “This email looks suspicious.” She clicks through anyway. She is not careless. She is exhausted. Between constant updates, complex login requirements, and mandatory training, her mental energy is gone.
This is security fatigue and it is one of the most underestimated risks inside organizations today.
What is Security Fatigue?
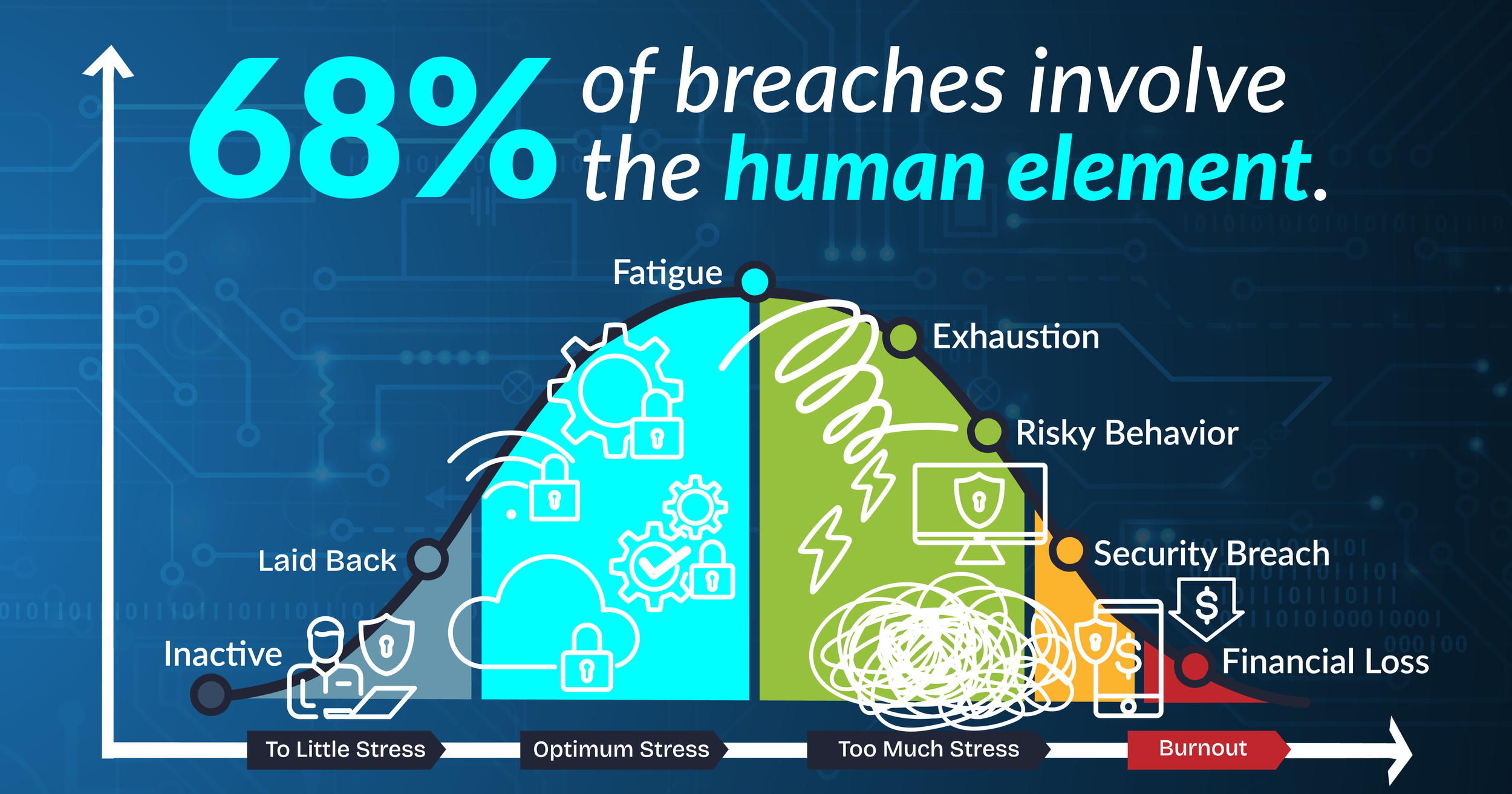
Security fatigue is the mental exhaustion caused by continuous exposure to security demands, warnings, and compliance tasks. NIST describes it as “a weariness or reluctance to deal with computer security” that leads people to risky shortcuts (1).
It shows up as:
Ignoring warnings or updates
Reusing weak or old passwords
Circumventing multi-factor authentication
Skipping through pop-ups without reading
Avoiding incident reporting
When employees disengage, even the best technical controls are undermined.
Why Security Fatigue is Growing
Alert Overload: Security tools flood users with pop-ups and prompts, many of them false positives. Over time, warnings lose credibility.
Complex Authentication: Frequent password changes, MFA prompts, and account lockouts create daily frustration. Gartner estimates 20–50% of IT help desk calls are password resets (2). Forrester places the cost at $87 per reset nearly $800 per employee annually (3).
Remote and Hybrid Work: Employees now juggle VPNs, collaboration platforms, and mobile devices under stricter policies. The added complexity fuels fatigue.
Training Fatigue: Annual awareness courses often feel repetitive and irrelevant. Instead of building security culture, they foster disengagement.
The Business Impact
Security fatigue is not just a user problem. It is a business risk.
Breach risk: In the Colonial Pipeline ransomware attack, one unused VPN account with a compromised password and no MFA triggered a national emergency (CISA).
Compliance risk: Frameworks such as SOC 2, HIPAA, and ISO 27001 require demonstrable human controls. If fatigue leads employees to bypass them, certification and audit readiness are compromised.
Financial risk: Verizon’s 2024 DBIR shows that 68 percent of breaches still involve the human element. Fatigue-driven negligence is a direct pathway to costly incidents.
When security feels like an obstacle, employees choose productivity over policy. Attackers count on that behavior.
How to Fight Security Fatigue
Simplify Security: Use passwordless authentication, single sign-on, and context-based access. Less friction means fewer shortcuts.
Design With Users in Mind: Apply human factors engineering. If MFA prompts or phishing simulations feel punitive, employees disengage. Build intuitive, minimal-friction experiences.
Modernize Training: Replace annual marathons with short, role-based, scenario-driven modules delivered throughout the year. Reinforce awareness without overwhelming.
Tune the Noise: Cut down on unnecessary alerts. Automate triage so employees only see high-quality warnings. Credibility comes from relevance.
Foster a Culture of Support: Move away from blame. Encourage reporting and recognize positive behavior. A culture of trust makes employees more willing partners in defense.
Key Takeaways
Security fatigue erodes human attention and weakens defenses.
It is growing due to alert overload, complex authentication, remote work, and uninspired training.
The impact is strategic: higher breach risk, regulatory exposure, and operational cost.
Leaders must invest in user-centered design, simplified workflows, and supportive culture to reduce fatigue and strengthen resilience.
Footnotes
NIST — “Security Fatigue Can Cause Computer Users to Feel Hopeless and Act Recklessly” (2016). Link
BleepingComputer — “Password reset calls are costing your org big money” (2022). Link
CIO — “The hidden costs of your help desk” citing Forrester (2024). Link